Deriving the most benefit from your security spend
Cyber-attacks towards enterprises or institutions are not new in this era of digital disruption. As a developing country with vast economic potential and a wide-range of digital innovations, Indonesia has been identified as one of the vulnerable countries that’s been targeted by hackers worldwide. A study by Frost & Sullivan, sponsored by Microsoft, forecast that the potential losses due to data breaches in Indonesia is around USD 34.2 billion, equivalent to 3.7% of the gross domestic product (GDP) of Indonesia at 2018. Pricewaterhouse Coopers (PwC) reported that cyber-attack in Indonesia focus on business information such as internal notes, employee database, customer databases, and intellectual property.
Not surprisingly, these studies drive enterprises to invest in cyber-security. According to Gartner’s 2017 research over USD 1.2 billion will be spent by corporates before the end of 2019 on equipment and personnel, an increase of over 18%.
At first glance, the cost to upgrade a company’s cyber-security fabric may seem unreasonably high however that is likely a small price to pay compared to the potential economic loss of being attacked. A successful attack can result in direct loss, extended downtime and even long term reputational damage. The World Economic Forum (WEF) forecasts the potential of loss due to cyber issues to exceed IDR 42 trillion.
Like any investment, upgrading your security infrastructure needs careful planning and a proper prioritization.
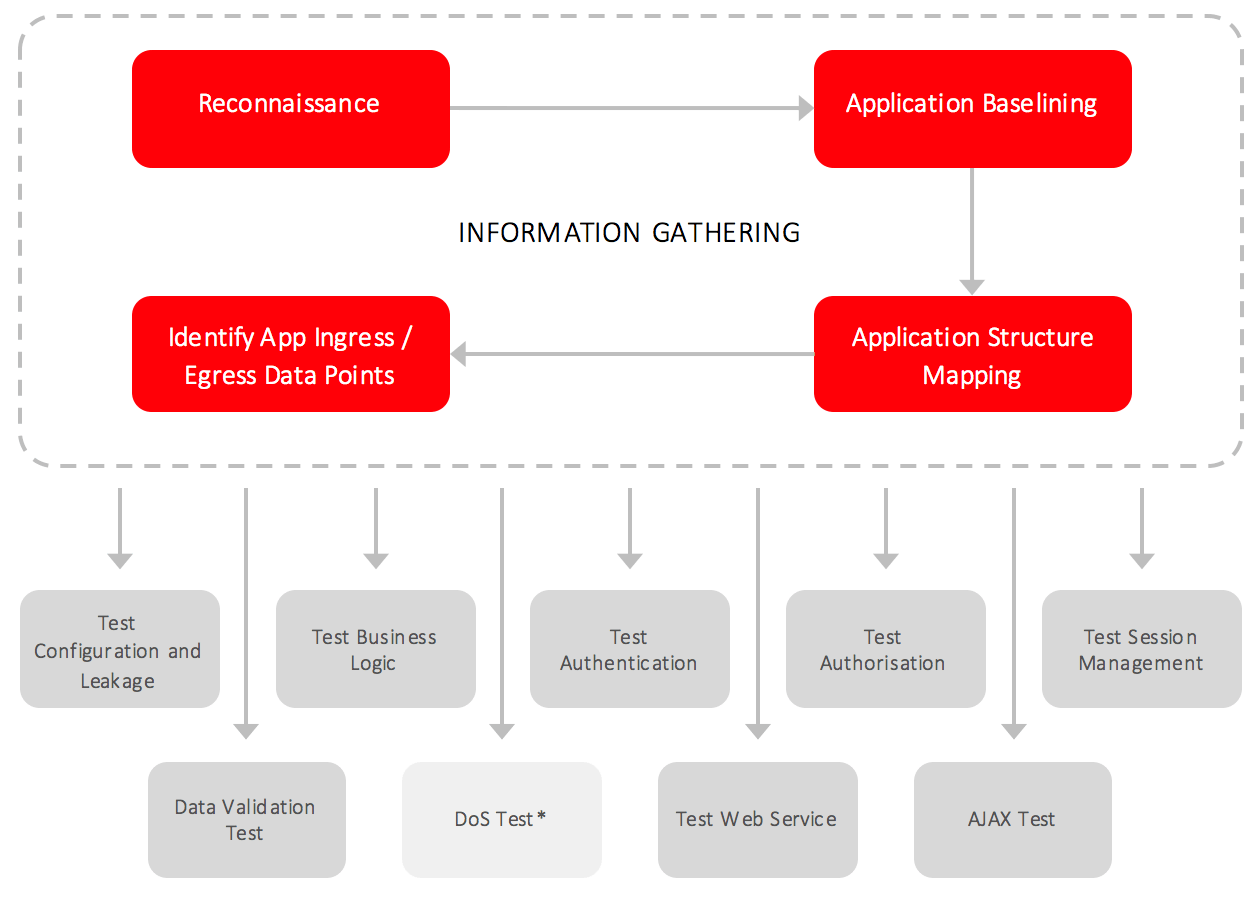
Penetration Testing as the Initial Investment
Penetration testing, or pen-test for short, is a service that should be undertaken by any enterprise to understand the vulnerabilities in their existing infrastructure, systems, and processes. The test will help enterprises assess their security protocols in an effective and practical way and give a clearer figure on where they should direct their efforts.
No single test can provide the necessary protection required to secure a company’s network infrastructure however pen testing is an integral component in establishing a comprehensive security protocol. It is a good first step in the journey to effective security and compliance.
The test involves simulating a cyber-security attack in order to (1) understand the existing security vulnerabilities, (2) determine what attacks are likely and (3) the impact of the attack on the enterprise. The weak points of the system will be the entry point of the attacker, these may be the result of a network vulnerability, poor processes or simply human error. For applications or infrastructure that is under development, penetration testing is best carried out within the staging environment prior to live deployment.
Most companies, especially those within industries that require the tightest security, understand the importance of penetration testing to gain insight into their security posture. What is sometimes missing is the objectivity that can be brought by employing an independent 3rd party to carry out the test.
An IT guide book from the Federal Financial Institutions Examination Council’s (FFIEC) in America, states that security system testing by an independent party greatly enhances the credibility of the result. It goes on to say that those third parties should not be affiliated directly or involved in the design, installation, maintenance or operation of the system being tested.
Security Penetration Testing Service by Telkomtelstra
Penetration testing is one of a number of tailored Security services offered by telkomtelstra. It can be used as a standalone test or part of our comprehensive end-to-end solution.
By performing a simulated attack our team can identify weaknesses that might serve as an entry point for a hacker to penetrate your systems. By pinpointing these vulnerabilities, we can flag any imminent risks and recommend ways to improve your overall security posture.
For instance, it is very likely that you have an application or service that is accessible via the public internet. Whilst that may not be a problem, it does provide the potential for malicious attacks into your network and beyond, into your systems and applications.
A penetration test can have two outcomes; it can identify weaknesses in your security fabric that require resolution or, hopefully, provide you the peace of mind that your infrastructure is secure.